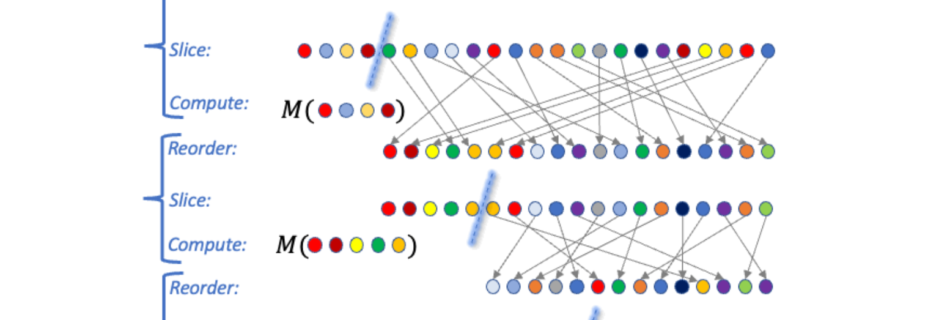
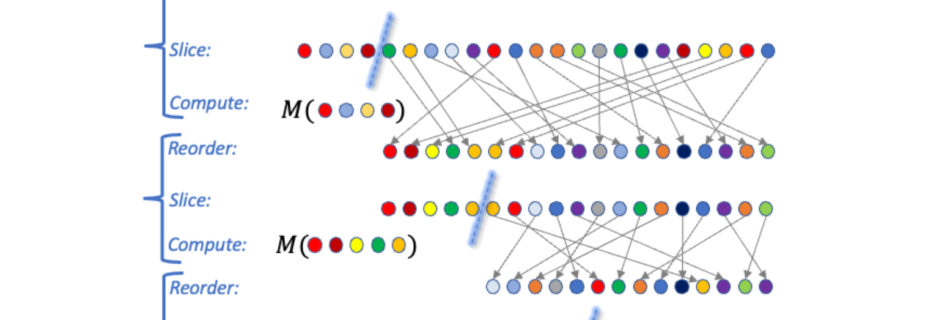
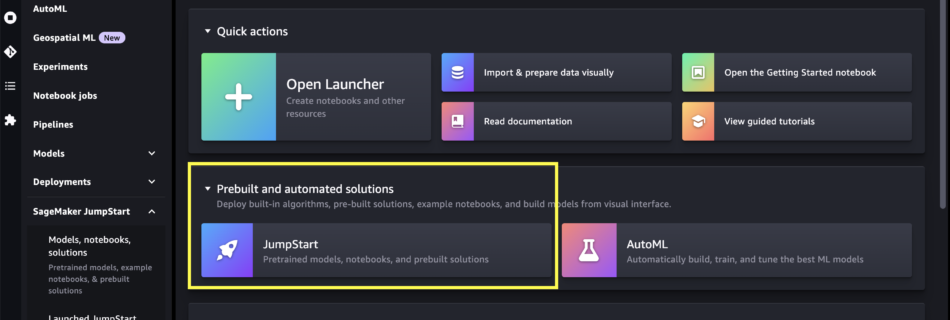
Amazon SageMaker simplifies the Amazon SageMaker Studio setup for individual users
Today, we are excited to announce the simplified Quick setup experience in Amazon SageMaker. With this new capability, individual users can launch Amazon SageMaker Studio with default presets in minutes. SageMaker Studio is an integrated development environment (IDE) for machine learning (ML). ML practitioners can perform all ML development steps—from preparing their data to building, …
Read more “Amazon SageMaker simplifies the Amazon SageMaker Studio setup for individual users”